How the proliferation of security threats and spending has created a $2 trillion opportunity
Part one of our two-part deep dive into security, starting with the status quo and five areas we think present the biggest potential for disruption.

Thanks to our MBA intern Shyam Anjaria, who co-authored this piece.
Security leaders are tasked with a critical job: securing the internet. But that job is becoming more complex. Cyberattacks are growing in number, thanks to the expansion of cloud infrastructure and connected devices. And they’re becoming more sophisticated, as bad actors leverage new technologies like Generative AI (GenAI) to find and exploit vulnerabilities at scale.
As a result, security is entering a new phase: one that prioritises connected and asset-light workflows to maximise efficiency while minimising risk. We believe there’s a $2 trillion opportunity on the table for disruptors who can deliver that value in five key areas. Let’s take a look at the state of play in security today – and where innovators can make the most impact.
The status quo of security
Organisations understand that cyber insecurity poses significant long- and short-term risk. Damages are estimated to cost ~$8 trillion globally each year, with an annual growth of 15%. To defend against this risk, security leaders have invested in an ever-evolving arsenal of apps and infrastructure over the last few years.
But the proliferation of third-party software is driving up costs, enlarging attack surfaces and introducing more potential vulnerabilities. At the same time, bad actors are using GenAI to develop new threats that organisations don’t yet fully understand, and can’t protect against. GenAI, while focusing attention and intelligence on the attack surface, also enables attackers to identify vulnerabilities at a speed and scale that defenders can’t match. Add to this the persistent threat of human error and insider risk, and security leaders are finding themselves (and their budgets) stretched thin.
They’re restrategising in response. Organisations are expected to expand their budget lines across the security tech stack, in an effort to protect their data and infrastructure. In particular, they’re focusing on finding more efficient third-party risk management solutions, as well as effective insider risk management programs.
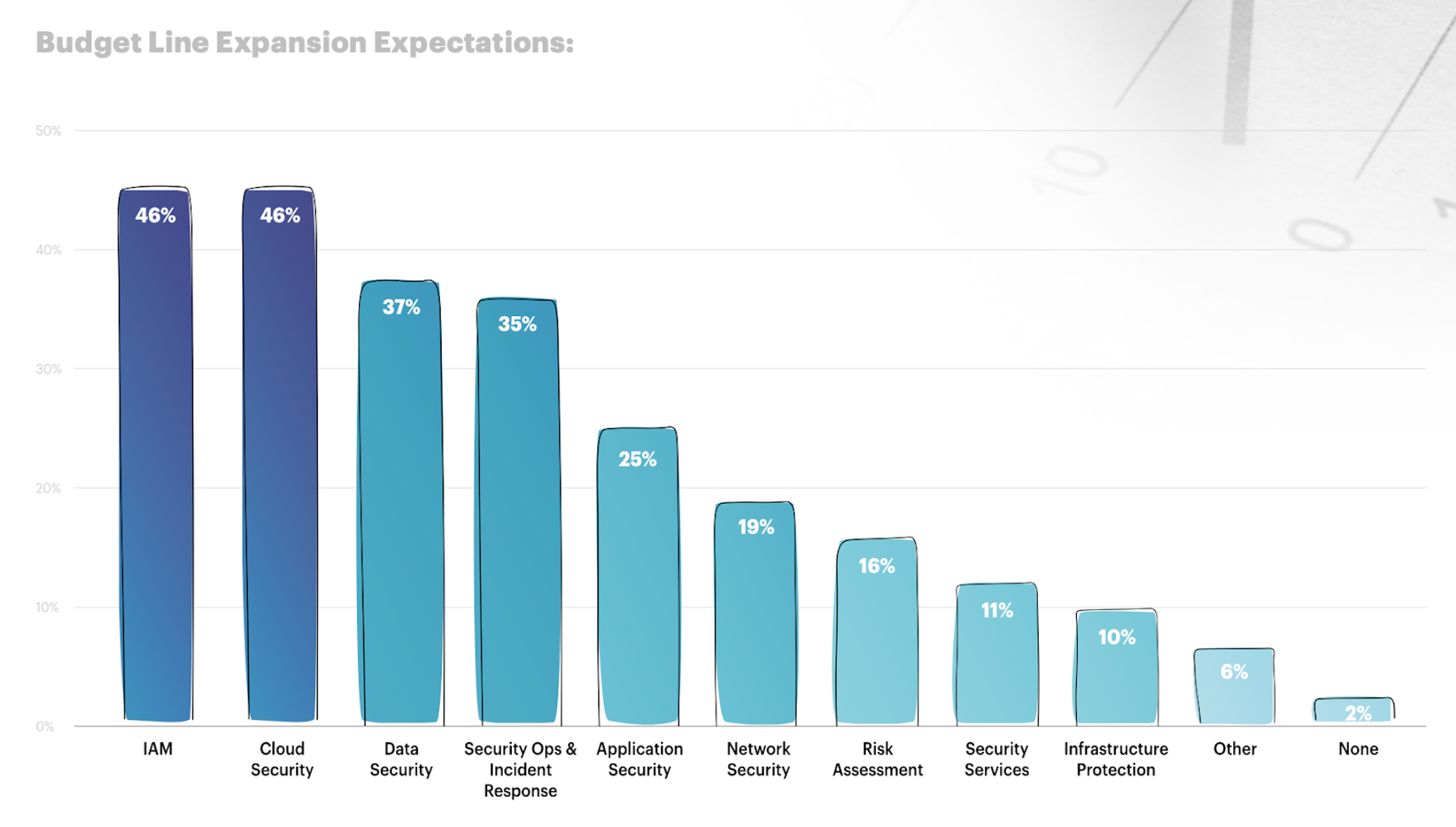
We’re seeing significant change across five key sectors:
- Cloud Security
- Identity and Access Management
- DevSecOps
- Security of Things
- AI Security
Let’s deep dive into each to understand why they’re primed for disruption, and where opportunities exist for founders and their products.
1) Cloud security
Cloud adoption is skyrocketing. Once the reserve of small, low-risk applications and experiments, more and more business-critical initiatives are now moving to the cloud. Enterprises are migrating legacy software to cloud environments, and increasing their investment in cloud infrastructure.
But security practices to protect the cloud aren’t accelerating at the same pace. 45% of enterprises are either in the earlier stages of initiating cloud security practices, or haven’t started at all. That exposes them to serious security and operational risk. Data breaches cost each enterprise around $4.5m annually – a number that’s growing 15% year on year.
There’s a clear need for solutions that allow enterprises to reap the benefits of moving to the cloud while retaining control over their security posture, data protection programs, and application integrity. Today, solutions like PANW, Wizz, and Orca enable visibility, discovery and monitoring. The next step will be AI-driven breach remediation – a trend that’s already emerging to help cut costs, while ensuring regulatory compliance.
Opportunities
Organisations are tackling SaaS sprawl and the associated risks by consolidating their tooling. Cloud security is no exception: by 2026, 80% of enterprises will be using three or fewer vendors, as opposed to the current average of ten. The tools they keep will be those that deliver on three criteria:

We can expect to see monitoring, discovery, identity management and configuration tools converge to provide a comprehensive suite of cloud security services.
Cloud Native Application Protection Platforms (CNAPP) which combine application security testing, cloud configuration tools (CSPM, CIEM) and runtime protection tools (CWPP) will become increasingly attractive to security leaders seeking to protect their budgets and reduce backend complexity.
Zero-Trust Network Access (ZTNA) will also become crucial to protect against internal and external threats. ZTNA micro-segments access, removing implicit trust by continually verifying identities to keep networks, applications and data secure.
AI-driven cloud native detection solutions that take into account the differing attack surfaces in cloud environments will enable early detection, and prevent incidents or breaches. AI has a critical part to play in scaling defences.
2) Identity and Access Management (IAM)
IAM is the first principle in ZTNA. As ZTNA gathers pace, and the use of biometrics and identity verification within organisations grows, IAM tools are becoming vital. Cloud Identity Entitlement Management, behavioural biometrics and identity analytics are all paving the way towards passwordless authentication in the near future.
But IAM programs are beset by a handful of common challenges, which need to be solved if they’re to realise their full potential. It’s still difficult to balance robust security with a seamless user experience. Too much friction can increase, rather than decrease risk, if users feel it’s easier to work around controls like 2FA and MFA.
Typically, IAM governance and controls are implemented ad-hoc. The lack of centralisations creates compliance failures and security gaps, putting organisations at risk of breaches and subsequent fines. Similarly, this piecemeal approach results in missed opportunities to streamline and automate. Organisations can’t afford these operational inefficiencies, especially as the number of machine identities is on the rise.
Opportunities
Identity isn’t an easy area to disrupt. There’s uncertainty around the future of decentralised digital identity (DDID), with governments still testing technology and little clarity about how it will scale in the private sector. Meanwhile, the private sector is growing more complex. As legacy infrastructure transitions to a multi-cloud environment, configuring appropriate access management without introducing friction will be a challenge. Winning solutions will be those that make security postures more robust, while enabling seamless integration and oversight.
Passwordless authentication is gathering steam thanks to the FIDO2 standard. Solutions can add value by supporting multi factor authentication, as well as adding behavioural biometrics, risk-based authentication, or multimodal biometrics. Working in layers to create a minimally invasive, low-friction, but secure user experience is key.
IAM will form the basis for ZTNA frameworks. Integrating solutions to embed identity data into data protection and network forensics systems will be a pivotal first step towards identity-centric network access paths.
Continuous and custom identity-based verification journeys will enhance the value of IAM. No longer a binary and point-in-time workflow, authentication will evolve into an alternate risk engine that monitors risk signals on an ongoing basis, triggering relevant workflows accordingly.
3) DevSecOps
DevSecOps infuses security into the continuous integration and continuous delivery (CI/CD) pipeline, allowing development teams to address security challenges at DevOps speed.
Now a mature segment, SecOps teams have grown in size over the years to include multiple layers of governance and human intervention. Now, there’s a need to streamline, so that teams can more effectively balance the preemption, prevention, discovery, response and remediation of cyber attacks. Automation of Security Operation Centre (SOC) is a growing trend, as is the adoption of security orchestration, automation and response (SOAR).

Opportunities
As elsewhere, AI is a critical enabler as DevSecOps becomes more integrated and mature. Freeing up team time to focus on strategic initiatives, while operational functions are left to automated systems, will enable organisations to respond to security threats with greater precision and agility.
Infrastructure as Code (IaC) utilises configuration files to automate the management and oversight of infrastructure. The constant release of new apps and updates can become burdensome for engineers to manage. IAC means they can allocate their time more efficiently, so they can maximise the potential of cloud computing instead of getting stuck on admin.
Enhanced Software Bill Of Materials (SBOMs) will resolve the current issues around consistency in data provision that plague automated SBOM generation. The value of SBOMs is limited: they require frequent updates to remain relevant in procurement decisions. Solutions that can integrate additional tools (such as software composition analysis and code signing) have an important role to play in establishing a well-managed and secure software supply chain.
Threat Intelligence, Analytics and Remediation tools that support DevSecOPs teams to analyse patterns, anomalies, and threat indicators will help make organisations’ security postures more robust. The ability to proactively identify potential risks, and take measures to mitigate them is essential as security threats become more sophisticated.
4) Security of Things (Secure IOT/IIOT)
The number of connected devices across public and private infrastructure is growing exponentially. It’s estimated that today, there are a total of 31 billion managed and unmanaged IoT devices across the world, and more being added every year.
With more devices comes more ransomware: 700% more in the last five years alone. As the risk of data breaches and damages grows, there’s an urgent need to protect devices. And there’s a huge opportunity for founders and products that can rise to the challenge: the IOT Security market is worth $20 billion.
Opportunities
Typically, IOT security solutions are highly verticalised, thanks to the complexity of regulatory and compliance regulations across sectors. Building with those verticals in mind will be important to unlock scale, as will streamlining discovery, monitoring and threat detection processes.
AI-based threat remediation will make Secure IoT more responsive and scalable. Integrating a ZTNA strategy to automatically remediate threats will enable protection in real time, and efficiently control risk.
Verticalised platforms for physical devices will accelerate Go To Market strategies and shorten sales cycles. Solutions that are tailored to the nuances of physical assets across verticals are better-equipped to manage regulatory policies and integrate into existing processes.
5) AI Security
The adoption of GenAI within organisations has been rapid, and isn’t set to slow. By 2026, over 80% of enterprises will be leveraging generative AI models, APIs, or applications, up from less than 5% today. But as with cloud security, tools to protect these new technologies are proving slower to emerge. Of the organisations currently leveraging AI, only 38% mitigate security risks, and just 32% are working to address model inaccuracy.
That’s a problem. AI raises a huge new range of critical considerations in terms of security, ethics, privacy, and risk management, all of which need to be intelligently managed. The use of GenAI to create more sophisticated phishing attacks, and to breach other LLMs and AI platforms, is a particularly urgent concern.
Opportunities
The only way to fight AI is to leverage AI. Soon, every security start-up will have to integrate an element of GenAI to combat AI-driven cyber attacks. AI can support with pattern recognition, enabling preemptive risk mitigation. It can also rapidly discover and monitor assets and their access levels, as well as automatically remediating critical attacks.
In short, AI’s a double-edged sword – but one security teams can wield to their advantage. As regulation and standardisation continues to evolve, two focus areas are emerging: security of AI, and AI for security.
Security of AI will be underpinned by cloud security. Using strong encryption and access controls is pivotal to ensure the security of the data used to train and operate AI systems. Models themselves will also need to be secured, using techniques like model obfuscation and watermarking. Finally, the interfaces and APIs with which users query models will need to be protected against interference to ensure only authenticated users can access them.
AI for security has enormous potential to disrupt almost every security category. Solutions that leverage AI to drive threat detection and discovery, as well as automating security posture recognition, will enable SecOps teams to intercept threats faster, and prioritise risk mitigation.
– – –
This is part one of a two-part series on security. Stay tuned for part two, where we’ll look in more detail at the themes emerging on the innovation side, pioneering early-stage businesses, and what makes a market-winning product.

